Microsoft Cloud for Sovereignty - Part 2 - Sovereign Landing Zone
Sovereign cloud series - Microsoft Cloud for Sovereignty - Part 2
This blog will give you an overview about the Sovereign Landing Zone. This information can also be found at Microsoft Learn.
What is Sovereign Landing Zone
A version of the enterprise-scale Azure Landing Zone designed for enterprises requiring advanced sovereign controls is called the Sovereign Landing Zone (SLZ). With Azure-native Infrastructure-as-Code (IaC) and Policy-as-Code (PaC) features, the SLZ assists enterprises in meeting their regulatory compliance needs. Utilising a configurable landing zone gives organisations the tools they need to enforce resources to be compliant with Azure Policy-defined policies, thereby addressing their demands for sovereignty.
Why use the Sovereign Landing Zone
Data can only remain sovereign when the owner has Full control over it. Full control in Azure refers to:
- Being the only entity that can grant the permissions necessary for users and workloads to access and process the data;
- Approving the regions that workloads can be deployed into.
At all levels, technical safeguards are required to prevent unauthorised data access. Therefore granting access to operators of cloud providers and managed service providers should also be explicit. The SLZ offers an architecture that can be deployed by a single script and customised using a single configuration file, allowing an organisation to satisfy their needs for sovereignty. These prerequisites for sovereignty are satisfied by combining:
- Aligning to the Cloud Adoption Framework to simplify adoption;
- Incorporating the technical guardrails provided by the policy portfolio, including the Sovereignty Baseline policy initiatives;
- Enabling policy configuration to allow organizations to customize their data sovereignty needs.
- Streamlining the use of Azure Confidential Computing services.
What is the difference between Sovereign Landing Zone (SLZ) and Azure Landing Zone (ALZ)
The SLZ uses the same code base as Azure Landing Zone (ALZ) Bicep and comes with:
- The Landing Zone Management Groups and Policy Assignments;
- Additional orchestration and deployment automation capabilities;
- An opinionated landing zone design for data sovereignty and confidential computing requirements;
- Additional Azure Policy Initiatives and Policy assignments to help meet sovereignty requirements for public sector customers, partners and ISVs.
When using Sovereign Landing Zone (SLZ) in place of the Azure Landing Zone (ALZ)
Recommendation guidelines from SLZ and ALZ teams are as follows:
- Use ALZ when you prioritize:
- Default option for most customers across various industries that can be built upon;
- Detailed configuration and customization options over the entire environment;
- Multiple deployment options including Portal, Bicep and Terraform;
- Default option for most customers across various industries that can be built upon;
- Use SLZ when you prioritize:
- Public sector customers focused on digital sovereignty requirements;
- Streamlined data governance capabilities enforced by policy and Azure Confidential Computing;
- Simplified deployment experience when using region-specific policy initiatives, like the Baseline informatiebeveiliging Overheid or BIO in Dutch;
- Deployment of workload templates to promote sovereign migration efforts.
- Public sector customers focused on digital sovereignty requirements;
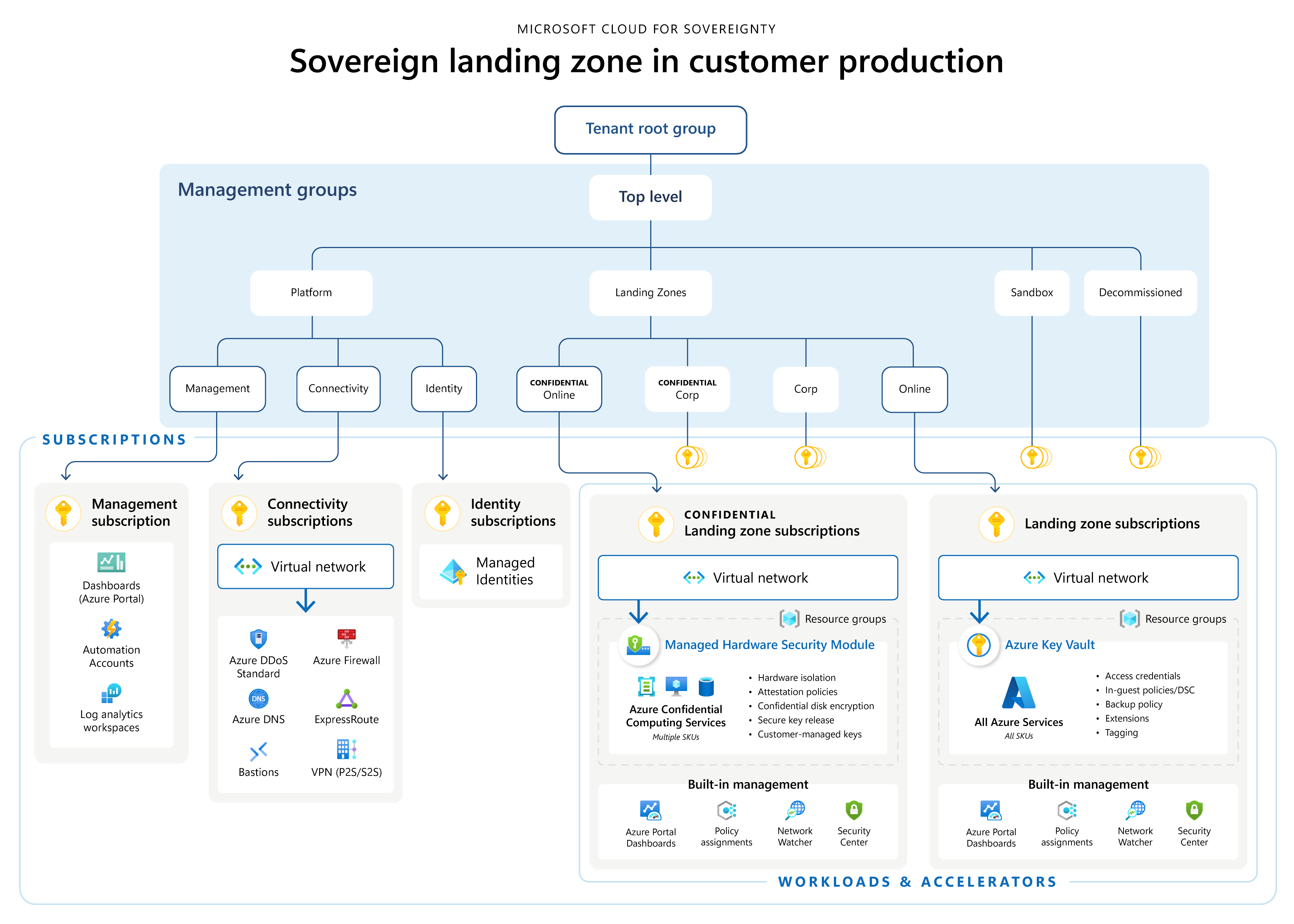
Sovereign landing zone design areas in more detail explained
The Azure landing zone architecture consists of eight design areas. Every design area outlines things to think about prior to deploying a landing zone. Additional factors to be taken into account when deploying the sovereign landing zone are covered in the following sections. Besides the Azure landing zone guidance, also keep these new considerations in mind.
Resource organisation
The following components will be deployed:
- Management groups for confidential compute - possibility to enforce for policy initiatives, offering controls such as resource deployment location, resource deployment types, and encryption;
- Microsoft Cloud for Sovereignty policy baseline
- Policy enforcement on confidential computing, protecting workloads at rest, in transit and while in use, which removes Microsoft from the trust chain.
- Location policies, which are also deployed by default to provide cloud admin control over where Azure resources can be deployed;
- Key management, which is controlled by a Federal Information Processing Standard (FIPS) 140-2 level-3 validated HSM and enforced by policy.
Network topology and connectivity
The sovereign landing zone focuses on operational control of data at rest, in transit, and in use. Components to take into consideration:
- Network traffic encryption - For best practices for network encryption, click here;
- Internet inbound and outbound connectivity - like Azure Firewall, DDOS and central Azure Bastion infrastructure.
Security
The sovereign landing zone architecture makes use of confidential computing in the confidential landing zones. The following sections describe services that provide support for Azure confidential computing:
- Azure Key Vault Managed HSM - requirement for deploying Confidential Computing resources. For design considerations and recommendations, click here.
- Azure Attestation - helps to confirm that a confidential VM runs on a hardware-based trusted execution environment (TEE) with security features like isolation and integrity enabled.
Governance
In most cases, Microsoft personnel perform operations, support, and troubleshooting, and no access to customer data is required. Occasionally, a Microsoft engineer needs to access customer data. These cases can come up in response to customer-initiated support tickets or when Microsoft identifies a problem.
- Customer Lockbox for Microsoft Azure - feature provides an interface that you can use to review and then approve or reject customer data access requests.
Platform automation and DevOps
The sovereign landing zone code is available as a GitHub repository. The landing zone can be deployed in its entirety or one piece at a time. You can incorporate individual component deployments into your current deployment workflow. For deployment guidance, click here. The GitHub repository includes the following sovereign landing zone components:
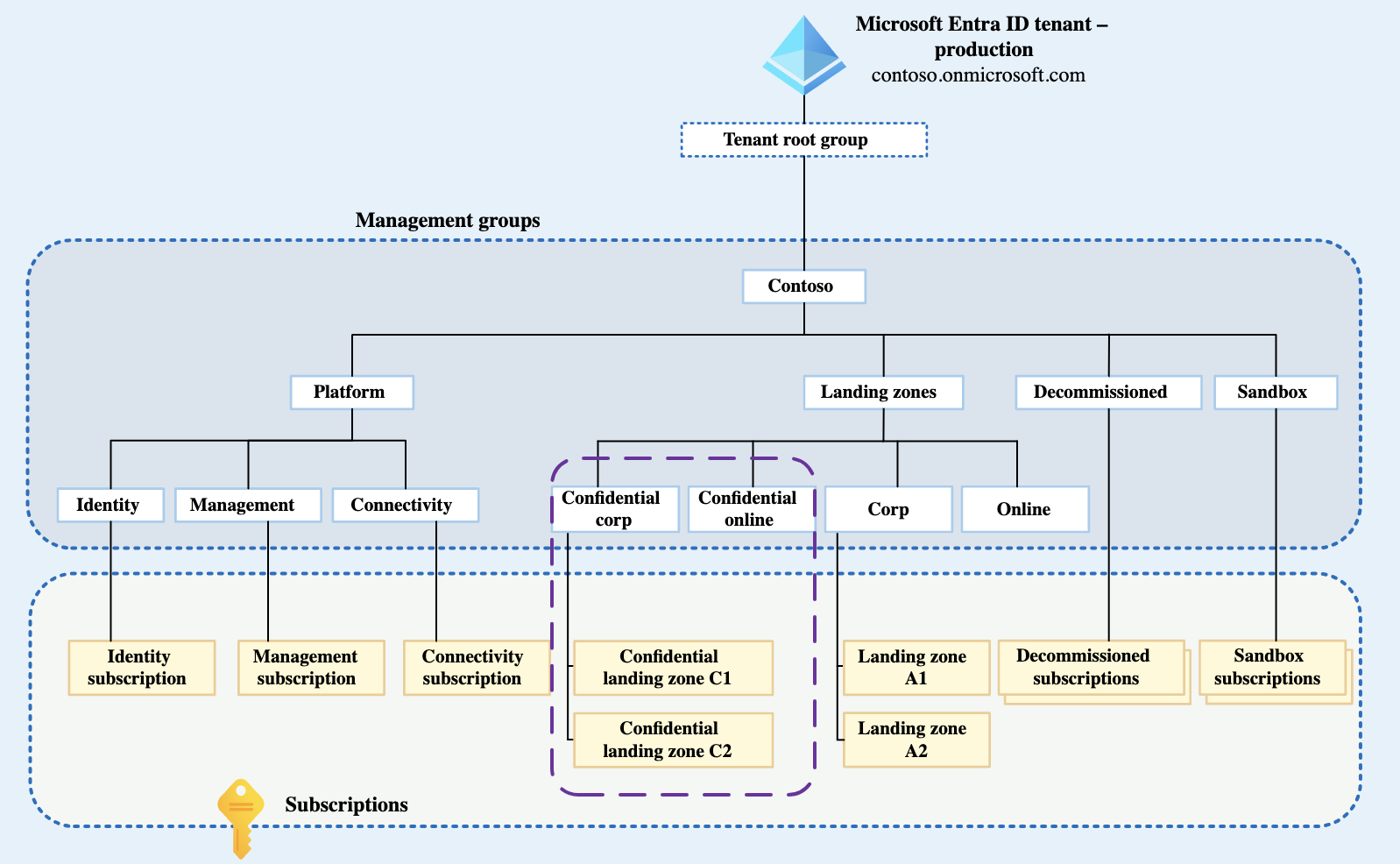
- Bootstrap: Sets up the management group hierarchy and creates the subscriptions as dictated by the architecture of the sovereign landing zone. These elements are deployed under the tenant root group of the Azure customer tenant;
Platform: Sets up the hub network and the logging resources that are used by the sovereign landing zone platform and workloads; - Compliance: Creates and assigns the default policy sets and the custom policies that are enforced in the environment;
- Dashboard: Provides you with a visual representation of your resource compliance.
Compliance Dashboard
A dashboard that assists you in verifying the sovereign landing zone in accordance with your equirements and local laws and regulations. In particular, the dashboard provides information about resource-level compliance with respect to:
- The baseline policies that are deployed with the sovereign landing zone;
- Other custom compliance that has been deployed.
Other tools
More tools are being released (currently in Public Preview) to help you further.
For more information, click here.