Microsoft Cloud for Sovereignty - Part 4 - Azure Attestation
Sovereign cloud series - Microsoft Cloud for Sovereignty - Part 4
This blog will give you an overview about Microsoft Azure Attestation. This information can be found at Microsoft Learn.
What is Microsoft Azure Attestation
Microsoft Azure Attestation is method for remotely confirming a platform's reliability and the integrity of the binaries running inside it. In simpler terms, attestation is a way of proving that a computer system is trustworthy. It is like passports and background check but then for computing.
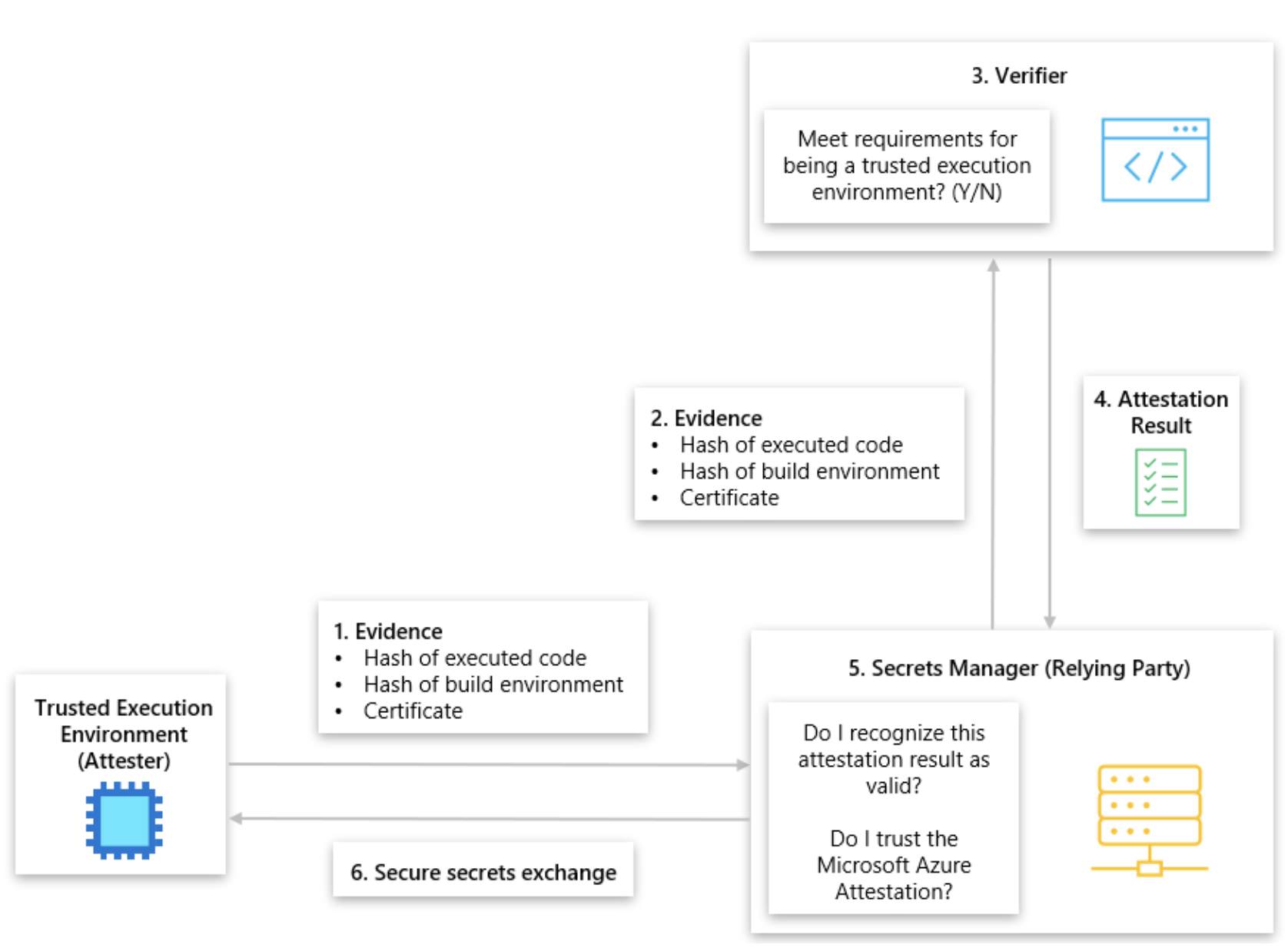
The practice of proving software binaries were correctly instantiated on a reliable platform is known as attestation. Remote relying parties can then gain confidence that only such intended software is running on trusted hardware. Azure Attestation is a unified customer-facing service and framework for attestation.
Azure Attestation is an enabler for Azure Confidential computing and Intelligent Edge protection. It receives evidence from compute entities, turns them into a set of claims, validates them against configurable policies, and produces cryptographic proofs for claims-based applications (for example, relying parties and auditing authorities). Azure Attestation supports both platform- and guest-attestation of AMD SEV-SNP based Confidential VMs (CVMs).
Why use Azure Attestation
Azure Attestation is the preferred choice for attesting TEEs as it offers the following benefits:
- Unified framework for attesting multiple environments such as TPMs, SGX enclaves and VBS enclaves;
- Allows creation of custom attestation providers and configuration of policies to restrict token generation;
- Protects its data while-in use with implementation in an SGX enclave or Confidential Virtual Machine based on AMD SEV-SNP;
- Highly available service.
Use cases
Azure Attestation provides comprehensive attestation services for multiple environments and distinctive use cases:
- SGX enclave attestation - Intel® Software Guard Extensions (SGX) refers to hardware-grade isolation, which is supported on certain Intel CPU models. SGX enables code to run in sanitized compartments known as SGX enclaves.
- Open Enclave attestation - a collection of libraries targeted at creating a single unified enclaving abstraction for developers to build TEE-based applications. It offers a universal secure app model that minimizes platform specificities.
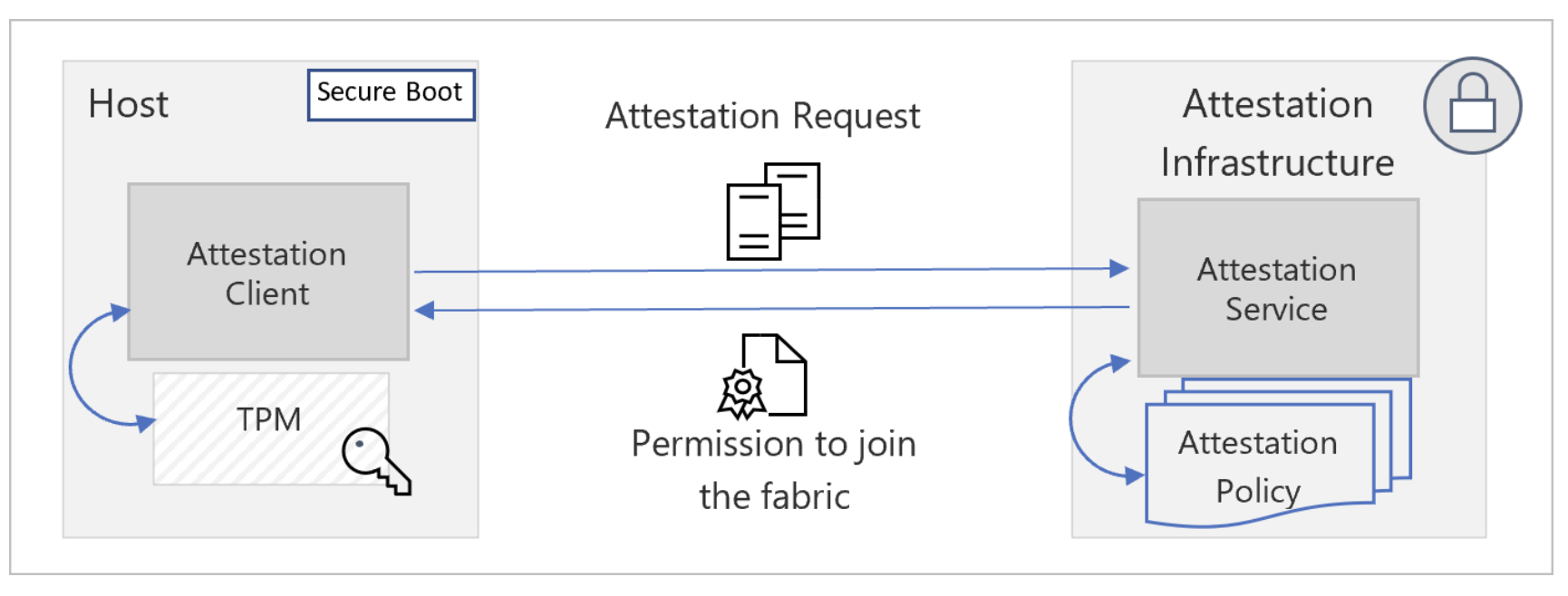
- TPM attestation - devices with a TPM can rely on attestation to prove that boot integrity isn't compromised and use the claims to detect feature state enablement during boot.
- AMD SEV-SNP attestation - Azure Confidential VM (CVM) is based on AMD processors with SEV-SNP technology. CVM offers VM OS disk encryption option with platform-managed keys or customer-managed keys and binds the disk encryption keys to the virtual machine's TPM. The service validates the measurements and issues an attestation token that is used to release keys from Managed-HSM or Azure Key Vault. The attestation and key release process is performed automatically on each CVM boot, and the process ensures the CVM boots up only upon successful attestation of the hardware.
- Trusted Launch attestation - Azure customers can prevent bootkit and rootkit infections by enabling trusted launch for their virtual machines (VMs). An attestation failure indicates potential malware, which is surfaced to customers via Microsoft Defender for Cloud, through Alerts and Recommendations.
- Azure Attestation EAT profile for Intel Trust Domain Extention (TDX) - Claims for an Intel® Trust Domain Extensions (TDX) attestation result genereated as an Entity Attestation Token (EAT) by Azure Attestation are described in this profile. The IETF JWT specification, the EAT specification, Intel's TDX specification, and Microsoft-specific claims are all included in the profile.
- Azure Attestation EAT profile for Intel Trust Domain Extention (TDX) - Claims for an Intel® Trust Domain Extensions (TDX) attestation result genereated as an Entity Attestation Token (EAT) by Azure Attestation are described in this profile. The IETF JWT specification, the EAT specification, Intel's TDX specification, and Microsoft-specific claims are all included in the profile.
Azure Attestation runs in a TEE (Trusted Execution Environments)
Azure Attestation is critical to Confidential Computing scenarios, as it performs the following actions:
- Verifies if the enclave evidence is valid;
- Evaluates the enclave evidence against a customer-defined policy;
- Manages and stores tenant-specific policies;
- Generates and signs a token that is used by relying parties to interact with the enclave.
Deployment
Deployment can be done via AzureCLI, PowerShel, Terraform, Bicep or via ARM. For more information, click here to reach the Microsoft Learn documentation. To learn how to build your own attestation policies, please click here for SGX or TPM.
Deep dive Azure Attestation
If you are interested in more deep dive into the Azure Attestation, click the following links for more information:
- Basic concepts how Attestation works behind the scenes;
- Basic concepts how Trusted Platform Module attestation works;
- How to establish trust with Azure Attestation;
- Business Continuity and Disaster Recovery (BCDR) support;
- Enable logging in Azure Attestation;
- Monitor Azure Attestation;
- How to perform TPM and VBS attestation;
- How to perform SGX attestation;
- Azure Attestation Workflow.
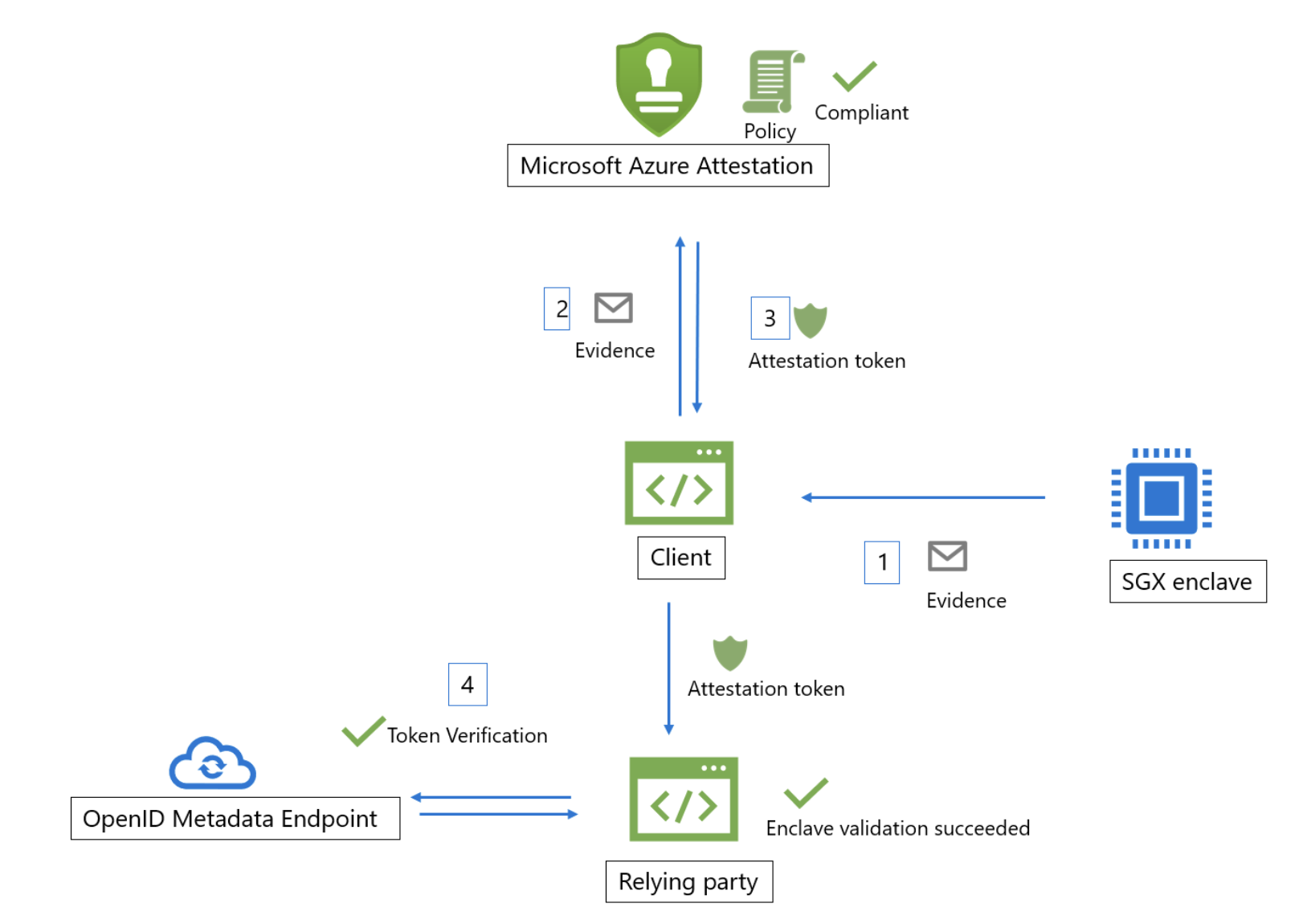
Useability of Azure Attestation in conjunction with Confidential VM's
Here are some usefull links from the Microsoft Learn, which explains more the useability:
- Cloud for Sovereignty - What is guest attestation for confidential VMs;
- Cloud for Sovereignty - Host Attestation Service explained.