Microsoft Cloud for Sovereignty - Part 5 - Azure Confidential Computing
Sovereign cloud series - Microsoft Cloud for Sovereignty - Part 5
This blog will give you an overview about Azure Confidential Computing. This information can be found at Microsoft Learn.
What is Confidential Computing
The Confidential Computing Consortium (CCC), a division of the Linux Foundation, created the industry term "confidential computing". They define Confidential Compute as: Confidential Computing protects data in use by performing computation in a hardware-based, attested Trusted Execution Environment. These secure and isolated environments prevent unauthorized access or modification of applications and data while they are in use, thereby increasing the security level of organizations that manage sensitive and regulated data.
Reducing the attack surface
The threat model seeks to undermine confidence or eliminate code and data access while it's being executed for a cloud provider operator or other actors in the tenant's domain. In Azure, this is accomplished through the use of a hardware root of trust that is not controlled by the cloud provider and intended to prevent unwanted access or environment manipulation.
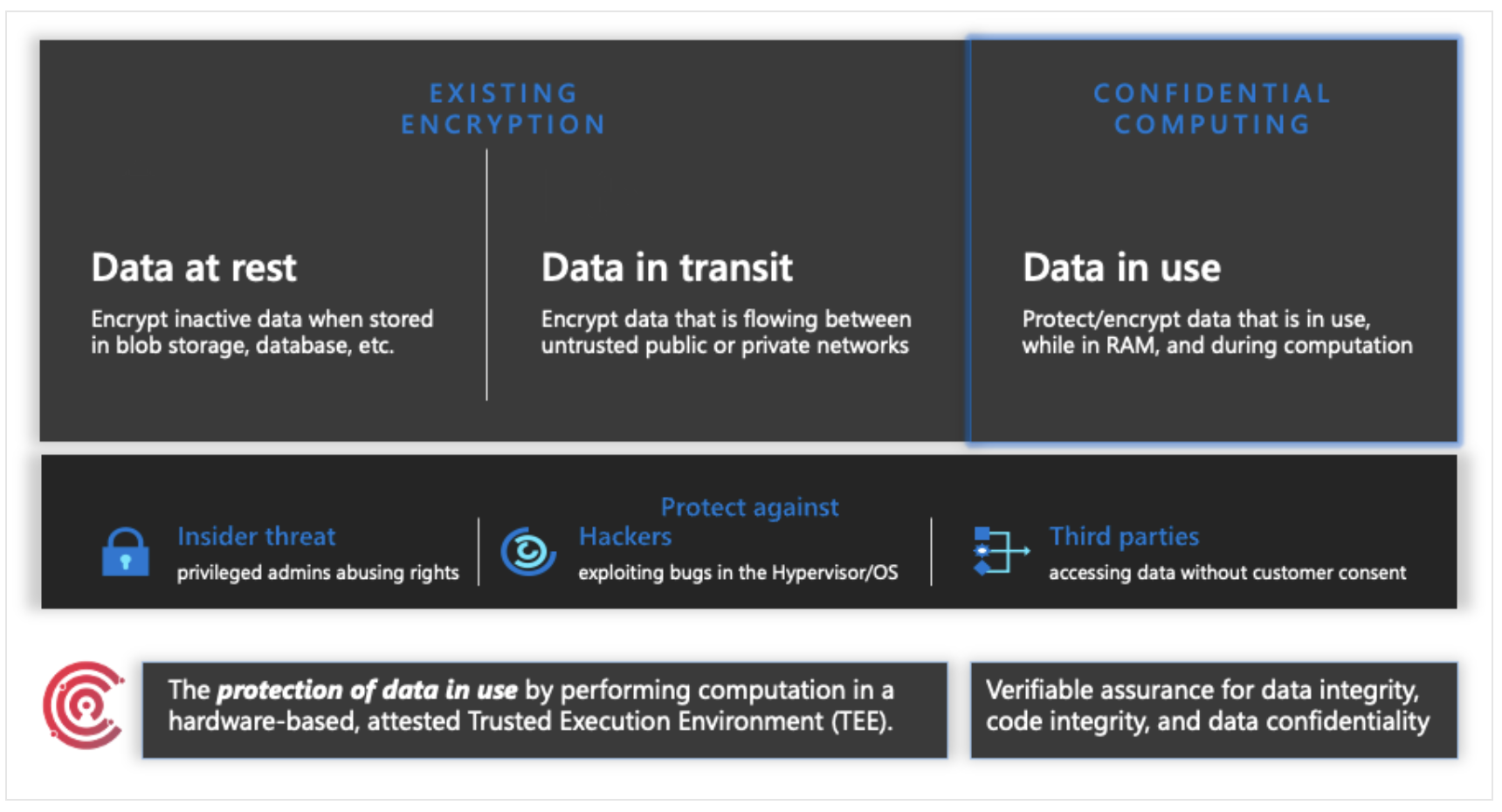
When used with data encryption at rest and in transit, confidential computing extends data protections further to protect data whilst it's in use. This opens up options for businesses looking to further secure critical information and apps hosted in cloud environments.
Usecases
You may protect your virtualized environment from the host, the hypervisor, the host administrator, and even the administrator of your own virtual machine by using confidential computing technologies. Microsoft provide a range of technologies based on your threat model that let you:
- Prevent unauthorized access: Run sensitive data in the cloud. Trust that Azure provides the best data protection possible, with little to no change from what gets done today;
- Meet regulatory compliance: Migrate to the cloud and keep full control of data to satisfy government regulations for protecting personal information and secure organizational IP.
- Ensure secure and untrusted collaboration: Tackle industry-wide work-scale problems by combing data across organizations, even competitors, to unlock broad data analytics and deeper insights.
- Isolate processing: Offer a new wave of products that remove liability on private data with blind processing. User data can't even be retrieved by the service provider.
Sovereign customers
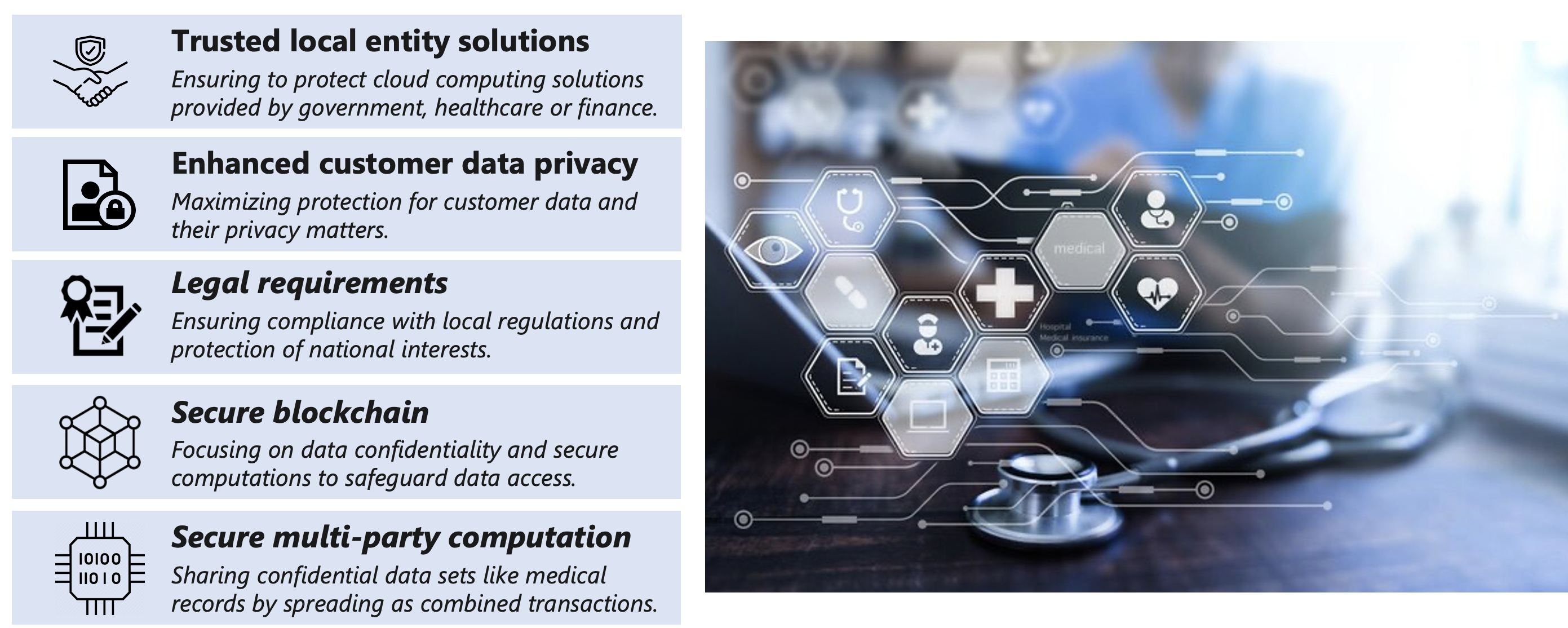
Confidential computing can apply to various scenarios for protecting data in regulated industries such as government, financial services, and healthcare institutes.

Scenarios
Below you can find common scenarios, which are intended to in spire you and give you a starting point, when building your applications with frameworks and services for confidential computing. Those scenarios can be found on MS Learn.
Confidential Computing on Azure
Microsoft Azure offers the following services with Confidential Compute:
Virtual machines and containers
- Confidential VMs using AMD SEV-SNP. DCasv5 and ECasv5 enable lift-and-shift of existing workloads and helps protect data from the cloud operator with VM-level confidentiality;
- Confidential VMs using Intel TDX. DCesv5 and ECesv5 enable lift-and-shift of existing workloads and helps protect data from the cloud operator with VM-level confidentiality;
- VMs with Application Enclaves using Intel SGX. DCsv2, DCsv3, and DCdsv3 enable organizations to create hardware enclaves. These secure enclaves help protect from cloud operators, and your own VM admins;
- App-enclave aware containers running on Azure Kubernetes Service (AKS). Confidential computing nodes on AKS use Intel SGX to create isolated enclave environments in the nodes between each container application.
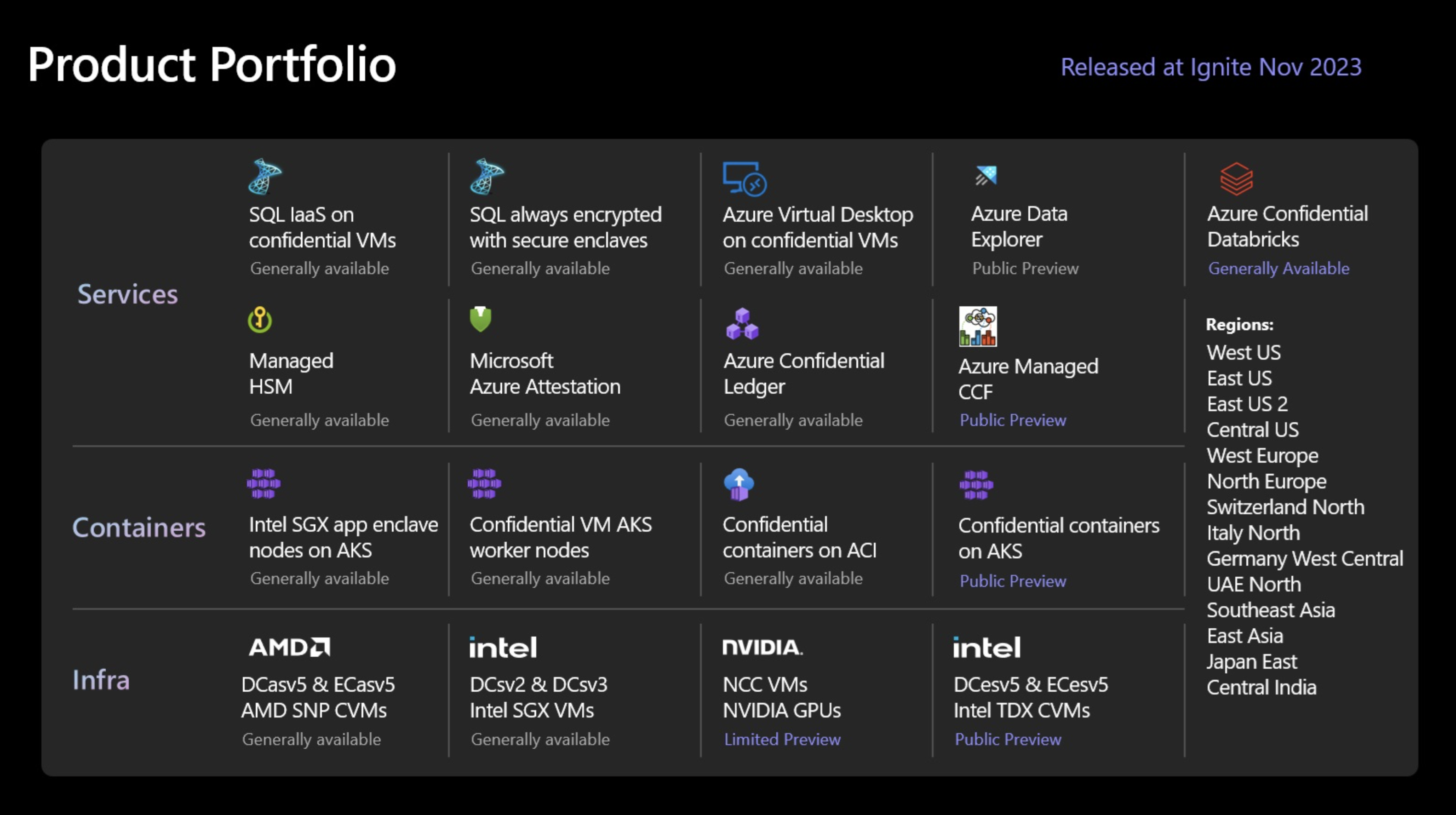
Confidential services
Azure offers various PaaS, SaaS and VM capabilities supporting or built upon confidential computing, this includes:
- Azure Key Vault Managed HSM, a fully managed, highly available, single-tenant, standards-compliant cloud service that enables you to safeguard cryptographic keys for your cloud applications, using FIPS 140-2 Level 3 validated Hardware Security Modules (HSM);
- Always Encrypted with secure enclaves in Azure SQL. The confidentiality of sensitive data is protected from malware and high-privileged unauthorized users by running SQL queries directly inside a TEE;
- Azure Databricks helps you bring more security and increased confidentiality to your Databricks Lakehouse using confidential VMs;
- Azure Virtual Desktop ensures a user’s virtual desktop is encrypted in memory, protected in use, and backed by hardware root of trust;
- Microsoft Azure Attestation, a remote attestation service for validating the trustworthiness of multiple Trusted Execution Environments (TEEs) and verifying integrity of the binaries running inside the TEEs;
- Trusted Hardware Identity Management, a service that handles cache management of certificates for all TEEs residing in Azure and provides trusted computing base (TCB) information to enforce a minimum baseline for attestation solutions;
- Azure Confidential Ledger. ACL is a tamper-proof register for storing sensitive data for record keeping and auditing or for data transparency in multi-party scenarios. It offers Write-Once-Read-Many guarantees, which make data non-erasable and non-modifiable. The service is built on Microsoft Research's Confidential Consortium Framework.
Supplementary offerings
- Azure IoT Edge supports confidential applications that run within secure enclaves on an Internet of Things (IoT) device. IoT devices are often exposed to tampering and forgery because they're physically accessible by bad actors. Confidential IoT Edge devices add trust and integrity at the edge by protecting the access to data captured by and stored inside the device itself before streaming it to the cloud;
- Confidential Inference ONNX Runtime , a Machine Learning (ML) inference server that restricts the ML hosting party from accessing both the inferencing request and its corresponding response;
- Trusted Launch is available across all Generation 2 VMs bringing hardened security features – secure boot, virtual trusted platform module, and boot integrity monitoring – that protect against boot kits, rootkits, and kernel-level malware.
Educational video's of confidential computing
More an easy learner via video's, check the following links:
- What’s new in Azure confidential computing;
- Azure Confidential Computing with Confidential VMs and AKS nodes | Azure Friday;
- Confidential Computing in Microsoft Azure - Who do you trust?.